Wie können wir helfen?
Basic 10: Encyption – Double Key
When using Microsoft 365, there are various options for encrypting Microsoft’s own systems, such as the Fort Knox principle or separate keys for each tenant (4 keys can also be contributed by the user) up to BYOK, HYOK and CYOK within Microsoft Information Protection. Now Microsoft has expanded the portfolio and brought a double key solution to the market.
Double Key Solution
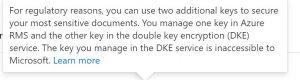
The Double Key solution uses two keys to encrypt data. One key is held by Microsoft and the second key is held by the customer. Access to the data is only possible with both keys.
In my surroundings it is already visible
All you have to do is create a new label or modify an existing one:
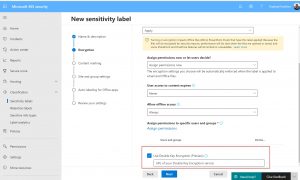
Help with setup and testing:
I followed the instructions and was able to set up the DKE service and use it today in Word and PowerPoint, for example. I also tested it with the UL scanner and it was also able to work with this form of label. It was also possible on the mobile phone (iOS).
But you need for all E5 licenses. (Microsoft 365 E5 and Office 365 E5)
External collaboration
The External collaboration isn´t possible. The Double Key solution is like a Hold-your-own-key solution, so that External User needs an Account into the hosted Tenant.
Impact on data protection and data security (Cloud Act?)
The function of the double key system can be very interesting especially for data protection, because it is possible as TOM (technical-organizational measure) to limit the access also from Microsoft. This includes above all a higher protection against disclosure to investigating authorities, because this is only possible if both keys are present and available. Microsoft alone and also the release of their keys to investigating authorities has no effect on our key. The file can only be opened with both keys. In this respect it could be a measure to defend against the Cloud Act and additionally to guarantee, besides the contract with MS, to always receive all requests.
Long term test and technical explanation
I will test it for you for 4 weeks and report then and also if it can really serve as TOM.


